
Ensure compliance with GDPR, PCI-DSS, and SEC regulations.
Protect sensitive data with strong encryption protocols.
Detects threats in real-time for quick response.
Manage access tightly with authentication and authorization measures.
Have a plan in place for a quick and effective response to cyber incidents.
Assess and manage cybersecurity risks associated with vendors and partners.
GetCoro checks all the business-critical security boxes for you. This is what we mean by holistic:
The GetCoro email and phishing prevention tool is remarkable. It seamlessly integrates with Office 365, analyzing incoming emails for spam or phishing attempts. We've opted for the premium package, granting us comprehensive monitoring by Coro's security experts, along with 24/7 support access. Their tool not only blocks certain domains or senders but also restricts specific global regions where malicious activities are common. We've even configured it to allow email traffic only from selected countries. This has significantly decreased phishing attempts from hackers. The interface is user-friendly and highly customizable, and the customer support is exceptional.
Protect PII, PHI, and PCI for patients and members
GetCoro serves as the focal hub for managing sensitive information, practice data, and user interactions, allowing you to uphold various security, compliance, and governance regulations.

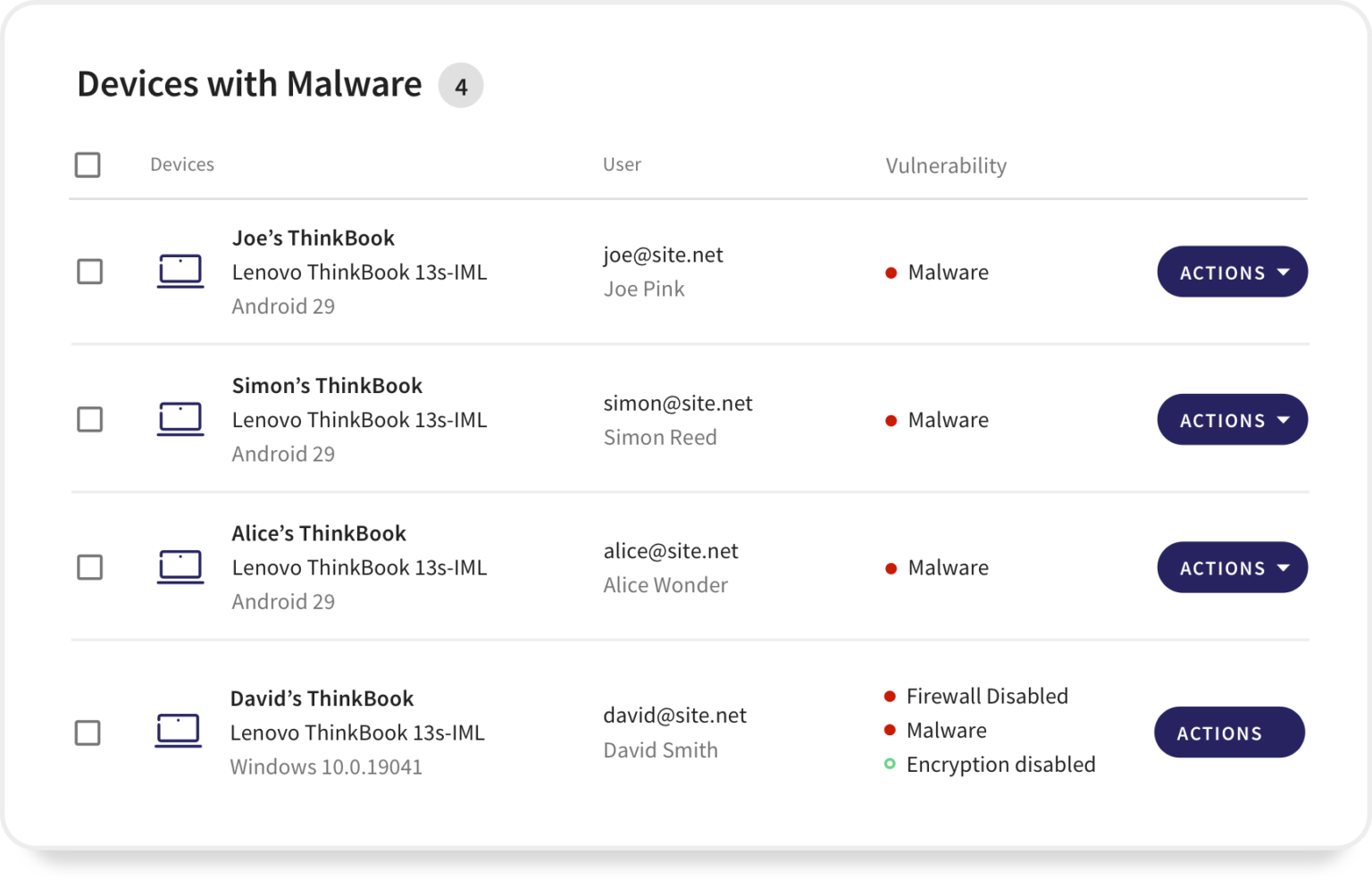
Detects possible malware and ransomware activities
Utilize GetCoro's pre-made templates for swift implementation of file policies and identification of distinct file extensions.
Automatically detect and contain malicious software
GetCoro employs AI technology to differentiate between actions performed by humans and those generated by bots. Coro actively identifies potential security breaches and takes immediate action by suspending suspicious users and halting any further tampering with files.
Control sharing permissions at the file, folder, and user levels
GetCoro guarantees proper sharing through collaboration guidelines that allocate precise authorizations to files, directories, and users, which also encompass whitelists for external contributors.
Automatically stop unauthorized sharing from occurring
It automatically restricts the extent of sharing permissions and cancels shared links to safeguard data and files.

Automatically identify behaviors that appear suspicious
Using behavioral patterns, GetCoro can autonomously identify compromised accounts or instances where insiders or privileged users pose a threat.
Instantly prevent phishing scams, ransomware, and malware attacks.
Our round-the-clock monitoring ensures prompt detection and blocking of suspicious email activities, with immediate notification to users.
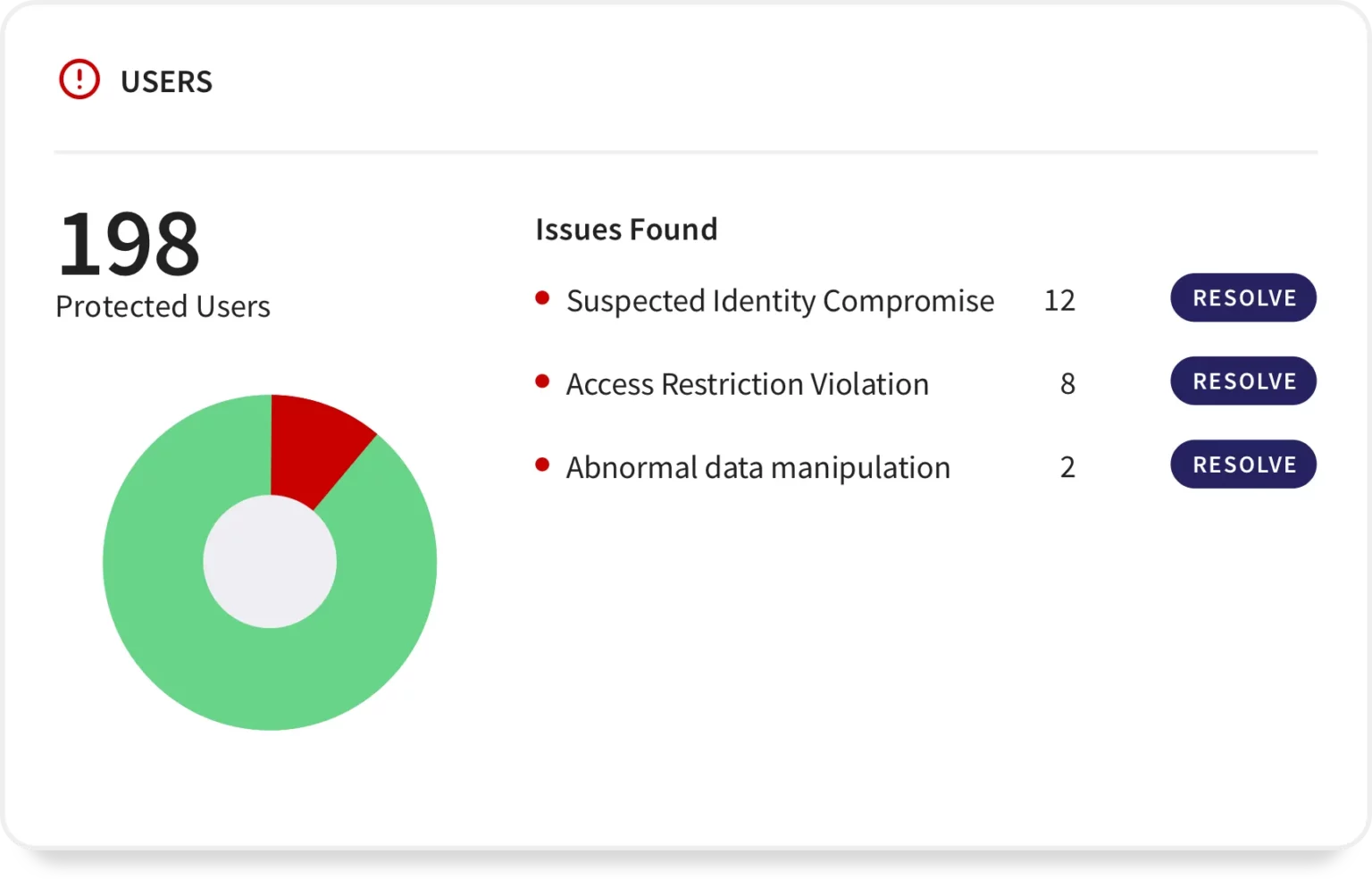
Firms in these sectors face risks such as data breaches, ransomware attacks, insider threats, phishing scams targeting employees, and regulatory compliance challenges. These threats can result in financial losses and reputational damage.
Embark on your journey towards enhanced cybersecurity solutions with the guidance and support of our experienced team.
Let’s Talk