
Safeguard your users and devices, whether in-office or remote, from ransomware, phishing attacks, compromised accounts, and internal threats - all while staying cost-effective. Cyber attacks often target software technology companies. Don’t allow advancing threats to compromise your IT team, users, or business operations. Counter malware, ransomware, and phishing efficiently with a single intelligent solution. GetCoro delivers advanced cyber defense tailored for software technology companies
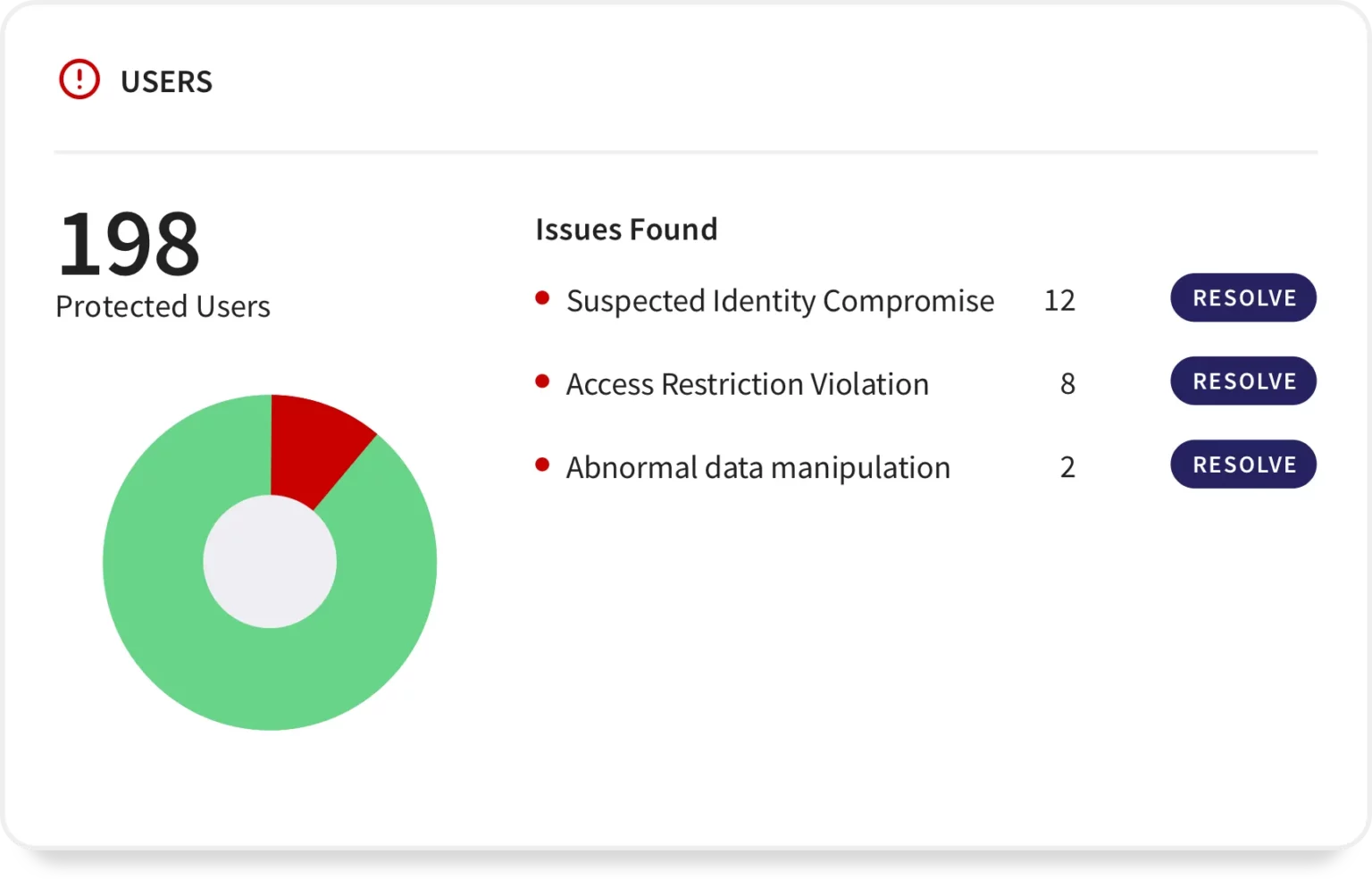
Users are safeguarded with advanced security measures for seamless online interactions and secure access to sensitive information.
Cloud applications are shielded against cyber threats to ensure uninterrupted workflow and data integrity in financial and legal operations.
Email security is fortified to prevent phishing attacks and malware infiltration, safeguarding communication channels crucial for business transactions.
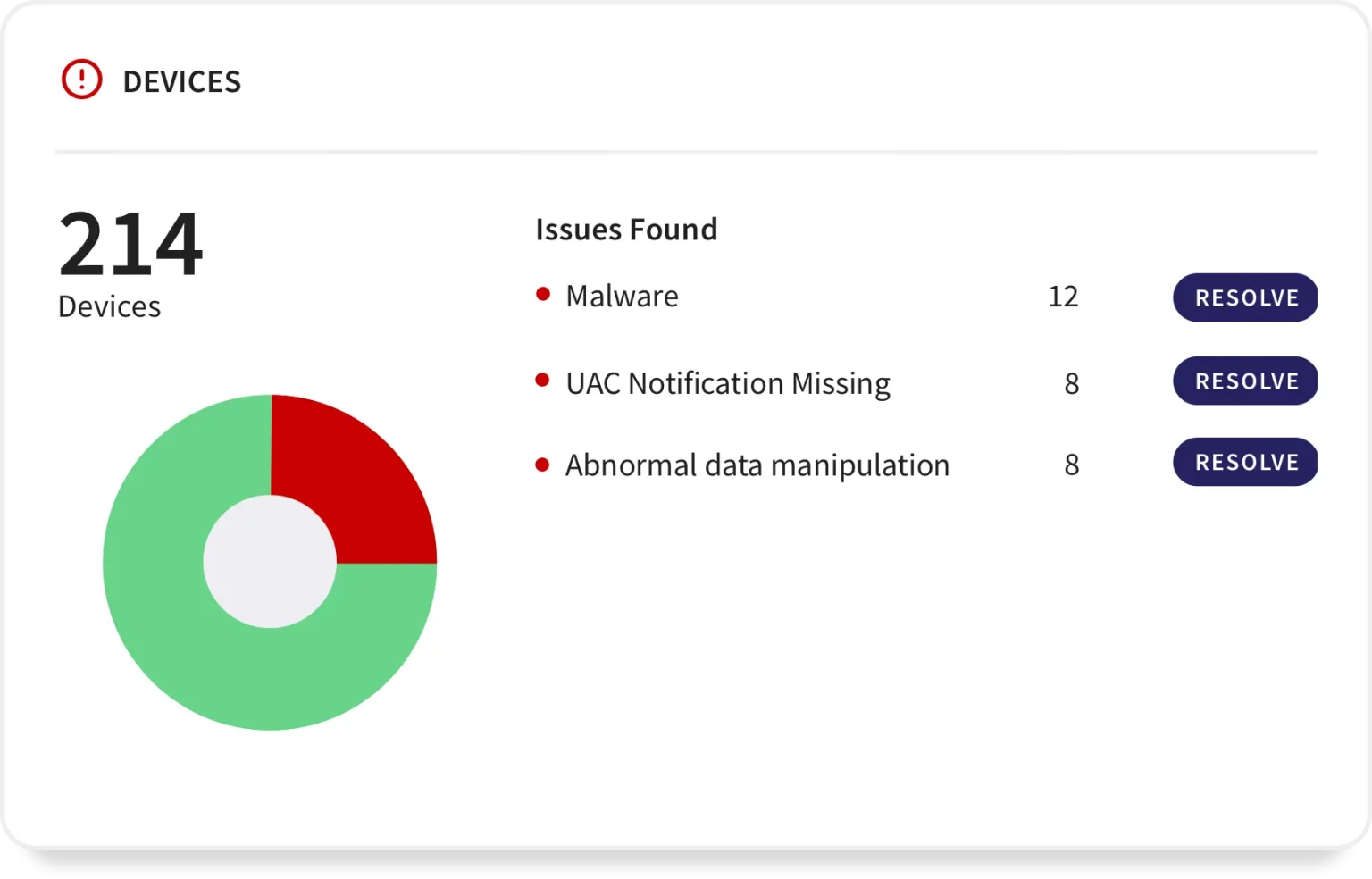
Devices fortified with robust defenses to uphold confidentiality and protect against unauthorized access to critical systems and data.
Data is protected with encryption and access controls to maintain confidentiality, integrity, and compliance with regulatory standards in financial and legal sectors.
GetCoro checks all the business-critical security boxes for you. This is what we mean by holistic:
The GetCoro email and phishing prevention tool is fantastic. It fully integrates with Office 365 to analyze incoming emails for spam or phishing attempts. We pay for the premium package, which gives us full monitoring from GetCoro's security experts. We have access to their support 24 hours a day, 7 days a week. Their tool has the ability not only to block certain domains or senders, but it can block out specific regions of the globe where bad actors typically do their dirty work. We even have it locked down to only allow email traffic from certain countries. It has dramatically reduced our incoming phishing attempts by hackers. Very easy-to-use interface. Very customizable. Customer support is awesome.
Protect yourself against rivals, cybercriminals, and even governmental entities aiming to abscond with your precious intellectual property and data. GetCoro identifies suspicious actions, malicious software operations, and unauthorized data dissemination, promptly putting an end to them.

Automatically detect suspicious behavior
GetCoro employs behavioral models to autonomously identify instances of compromised accounts or when an insider or confidential user exhibits threatening behavior.
Instantly lock down suspicious accounts
Take action by suspending doubtful user accounts or revoking file access permissions to safeguard data and systems.
Identify potential malware and ransomware activity
Leverage GetCoro's preconfigured templates for swift implementation of file policies and identification of distinct file extensions.
Automatically detect and contain malicious software
With its AI-driven process, GetCoro seamlessly contrasts between human and bot-generated activities. It detects potential threats and promptly mitigates them by suspending suspicious users and halting further file corruption.
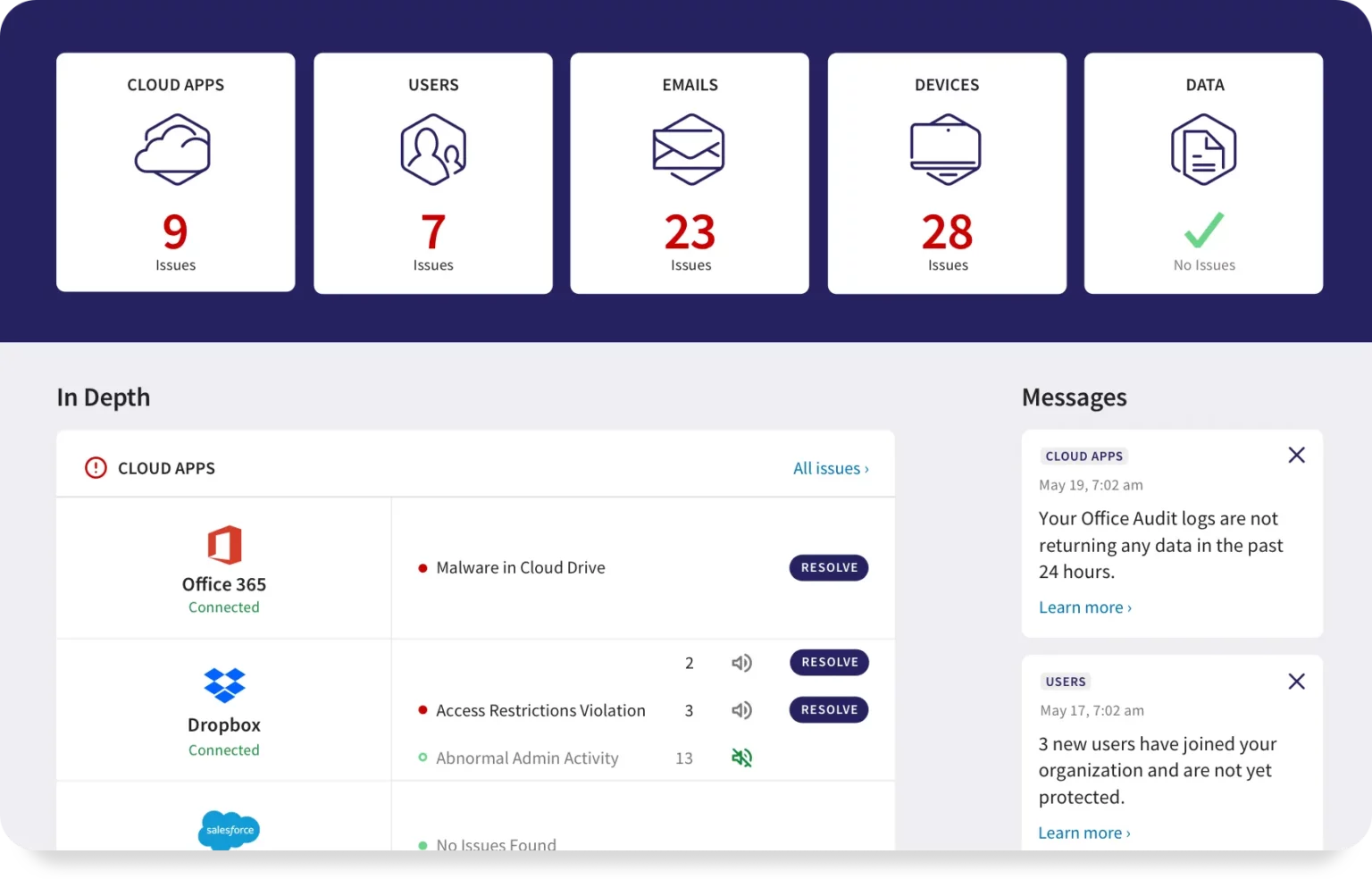
Dashboard with flexible widgets and mobile app helps prioritize risk
Steps to prepare for cybersecurity incidents include developing and testing an incident response plan, establishing clear roles and responsibilities for incident response team members, conducting tabletop exercises and simulations, and ensuring that backups of critical data are regularly updated and securely stored.
Embark on your journey towards enhanced cybersecurity solutions with the guidance and support of our experienced team.
Let’s Talk